At 10-Year Milestone, Microsoft's Trustworthy Computing Initiative More Important than Ever - Stories

Trusted Path and Trusted Channel by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu

Trusted Computing Platforms: TPM2.0 in Context: Proudler, Graeme, Chen, Liqun, Dalton, Chris: 9783319087436: Amazon.com: Books
All new Windows 10 PCs to have Trusted Platform Module 2.0 enabled by default with Redstone - MSPoweruser
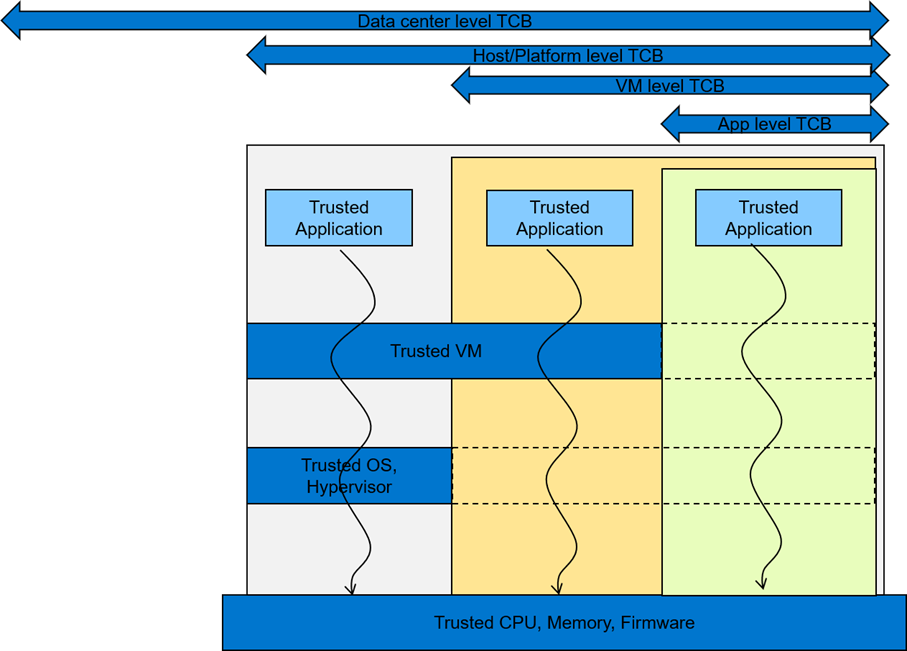
Understanding Confidential Computing with Trusted Execution Environments and Trusted Computing Base models | Dell Technologies Info Hub

Benefits of Using Trusted Computing Technology | Trusted Computing Platforms, the Next Security Solution | InformIT